There are many loopholes, and it is imperative for industrial security protection.
With the high integration of physical control and electronic systems, in the context of severe security threats, industrial control system security is related to national critical infrastructure security and people's livelihood security, and security management must be greatly strengthened. It is imperative to provide solutions and ground-breaking technical means for the network security problems faced by industrial control systems, and to improve the technical level of industrial control information security.
Industrial control information security issues are increasingly prominentFrom the point of view of the industrial control system itself, with the development of computer and network technology, especially the deep integration of informationization and industrialization, industrial control systems are increasingly using common protocols, general hardware and general software, through public networks such as the Internet. The connected business systems are also becoming more and more popular, which makes the attack behavior against industrial control systems increase greatly, and the vulnerability of industrial control systems is gradually emerging, and the information security problems are increasingly prominent.
The 2010 "Shenzhen" virus, the 2012 super virus "flame", the 2014 Havex virus and other viruses specifically for industrial control systems have caused huge losses to users, and also directly or indirectly threaten national security. . From the attack on Ukrainian power that occurred in 2015, we can see that it can affect the operation of the industrial control system without using complex attack methods and without completely restoring the operation process of the business system.

With the attention of all parties on the industrial control system, the loopholes in the industrial control system have been generally rising in recent years. However, due to the higher value of the industrial control system loopholes, there are still a large number of industrial control loopholes that have been discovered but not exposed. Therefore, the actual number of industrial control vulnerabilities should exceed the existing statistics. At the same time, SCADA, HMI, PLC, industrial switches, etc. account for the first few exposures. From the perspective of distributed vendors, Siemens, advantech, and scheider are still large vulnerabilities, and their total gaps account for nearly 30% of all industrial vulnerabilities.
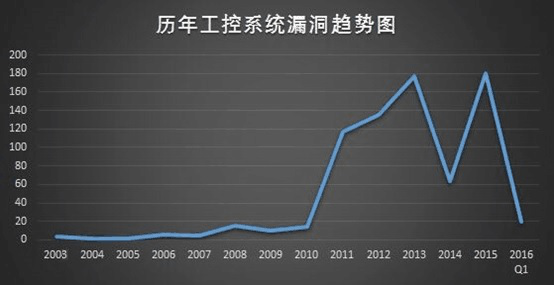
China is also suffering from information security loopholes in industrial control systems. For example, in 2010 Qilu Petrochemical, 2011 Daqing Petrochemical Refinery, and industrial control systems infected with Conficker virus, respectively, caused the control system server and controller communication to be interrupted to varying degrees.
Industrial safety policy, standards firstAlong with the guidance of national policies and the industry guidance for industrial safety in the industry, driven by relevant factors, the increase in the application examples of industrial safety products and the practical application results have been recognized by the industry. It is expected that the safety of industrial control systems will be in the near future. Will develop rapidly.
IEC 62443 is an industrial control system standard that is widely adopted and recognized internationally. All countries and industries to develop industrial control related standards and policies will refer to and absorb the concepts, methods and models provided by the standard. Whether you want to systematically understand the industrial security issues and their countermeasures, or want to understand some of the content, you can start from this standard.
The definition of information security for IEC62443 is:
A. Measures taken by the protection system;
B. The state of the system obtained by the measures to establish and maintain the protection system;
C. Be free from unauthorized access to system resources and unauthorized or unintended changes, damage or loss;
D. Based on the capabilities of the computer system, it can ensure that the unauthorized personnel and the system can neither modify the software and its data nor access the system functions, but ensure that the authorized personnel and the system are not blocked;
E. Prevent illegal or harmful intrusion into the industrial control system or interfere with its correct and planned operations.
Looking at the development trend of international industrial safety, the United States is the first country to start researching and implementing industrial safety standards. The North American Electric Reliability Company has given CIP series standards to carry out safety and safety inspections for power companies in North America (including nuclear power); Europe The safety of industrial control products has been tested according to the WIB standard, and the country represented by Germany has started construction of industrial safety based on ISO 27009 of ISO 27000 series; Japan has combined Achilles certification requirements based on IEC 62443 requirements, and has been stipulated since 2013. All industrial control products must pass the national standard certification before they can be used in China, and industrial safety inspection and construction have begun in some key industries such as energy and chemical industry; Israel has established a national industrial safety product safety testing center for industrial safety products before entering the network. Security detection.
In 2011, the Ministry of Industry and Information Technology issued the "Notice on Strengthening the Information Security Management of Industrial Control Systems" (Ministry of Industry and Information Technology [2011] No. 451), and put forward specific requirements for the safety management of industrial control for the first time. In recent years, with the continuous integration of information technology and industrial production activities, the industrial control security situation has become increasingly severe. The original No. 451 document has inadequacies such as lack of operation and insufficient technical skills in guiding the implementation of industrial security protection. The industrial safety control department and the industrial control system application unit are in urgent need of a simple, clear, easy-to-reach protection manual.
In 2016, for the information security market of China's industrial control system, it should be a very fruitful year. In particular, breakthroughs have been made in relevant laws, regulations and standards.
In October 2016, the Ministry of Industry and Information Technology issued the "Guidelines for Information Security Protection of Industrial Control Systems", which stated that industrial control system application enterprises should select and manage security software, configuration and patch management, border security protection, physical and environmental security. Safety control, protection, identity authentication, remote access security, security monitoring and emergency plan drills, asset security, data security, supply chain management, and implementation of responsibility. The publication of the Guide is an adequate implementation of the national key information infrastructure security protection requirements, and also provides an important reference for the industrial security protection work in the new era and the new situation.
On the basis of full consideration of operability, pragmatism and ease of implementation, the Guide puts forward 11 major and 30 small industrial safety protection measures, which provides an effective reference for the relevant units to carry out industrial safety protection work.
Enterprises must take the responsibility of the main bodyIt is much easier to implement information security for large distributed control systems (DCS) than programmable logic controller (PLC) systems, as most of them are deployed in large plants, and the design and installation of DCS systems is based on best engineering practices. Sexual standards and acceptance processes. Most of the PLC systems installed in the factory have no unified design, planning, implementation and acceptance. Because the purchase amount is relatively small, the management of installation and commissioning is relatively simple and rude, thus leaving many hidden dangers.
To prevent cyber attacks, information security projects require an effective and practical mechanism, including people, procedures, and technology. We can't expect most manufacturers to implement network information security projects on their automation systems very quickly.
From the nature point of view, industrial safety is the responsibility of production and operation, and industrial enterprises bear the main responsibility of industrial safety protection. Enterprises must establish and improve the enterprise's industrial safety production responsibility system, constantly improve the enterprise industrial safety management system, strengthen enterprise personnel management, supply chain management and system operation and maintenance management.
Industrial companies carefully study and discuss the IEC62443 standard and the "Industrial Control System Information Security Protection Guide", check the factory's automation system, evaluate the overall operation of the plant, identify possible hidden vulnerabilities, and discuss information with your team. Security policies and solutions that not only improve the efficiency of plant operations, but also prevent cyber attacks that may occur one day and protect plant assets, people and the environment.
It is necessary to do security protection from the entire life cycle of the industrial control system. Due to the increasingly close connection between various business links and related systems in industrial production, industrial control systems need to be protected in all stages of design, selection, construction, testing, operation, maintenance and disposal. Protective measures run through the entire life cycle of the industrial control system.
Industrial security protection should establish comprehensive protection capabilities from system and equipment security, network security, host security and data security. The traditional single-point protection can no longer cope with the increasingly severe security situation. The Guide proposes to establish protection capabilities on the core elements of industrial control systems and equipment, industrial networks, industrial mainframes, and industrial data, greatly improving the difficulty of hackers attacking industrial control systems. To effectively improve the safety level of industrial control systems.
It is necessary to speed up the cultivation of industrial safety professional technical teams. At present, there is a big gap in the risk assessment and protection plan planning and implementation of industrial control in China. When implementing the protective measures in the Guide, industrial enterprises urgently need relevant professional and technical personnel to carry out relevant work. Relevant competent departments should accelerate the construction of industrial security talents through various measures such as professional construction and talent cultivation.
Summary: With the continuous development of technologies such as informatization networking, it is also a general trend for control systems to access the Internet, so the information security of the control system and the ability to resist hacker attacks will be higher. Industrial enterprises can refer to the "Guide" to select industrial safety protection products or solutions, promote enterprises to implement industrial safety protection measures, and effectively improve the safety level of industrial control systems.
Wire to Board Connectors PDF Catalog
Wire To Board Connectors PDF Catalog Series are avialable in different terminations and sizes intended for use on a variety of applications. These connectors provide power and signal with different body styles, termination options, and centerlines. To find the wire to board set required, click on the appropriate sub section below.
Antenk offer Other Wire To Board Connectors like 3.91mm, 3.96mm,4.14mm, 6.2mm, 6.35mm, 10.0mm Available in Male Header, Female Header, Male Housing, Female Housing, Male Terminal, Female Terminal
3.91mm, 3.96mm,4.14mm, 6.2mm, 6.35mm, 10.0mm Wire To Board Connectors Straight type
3.91mm, 3.96mm,4.14mm, 6.2mm, 6.35mm, 10.0mm Wire To Board Connectors Right Angle type
3.91mm, 3.96mm,4.14mm, 6.2mm, 6.35mm, 10.0mm Wire To Board Connectors Male Housing
3.91mm, 3.96mm,4.14mm, 6.2mm, 6.35mm, 10.0mm Wire To Board Connectors Female Housing
3.91mm, 3.96mm,4.14mm, 6.2mm, 6.35mm, 10.0mm Wire To Board Connectors Male Terminal
3.91mm, 3.96mm,4.14mm, 6.2mm, 6.35mm, 10.0mm Wire To Board Connectors Female Terminal
Pcb Board Connectors,Other Wire To Board Connectors,Pitch Wire To Board Connectors,Jst Connector Wire To Board,4.14mm Wire To Board Connectors, 6.2mm Wire To Board Connectors, 10.0mm Wire To Board Connectors
ShenZhen Antenk Electronics Co,Ltd , https://www.coincellholder.com