Trusted Domain resolves the deadlock in the Internet

In October 2014, the news that China initiated the management of network ID cards (abbreviated as eIDs, all referred to as virtual identity electronic tags) was confirmed once again and has been piloted in many places. It is reported that the United States has initiated the management of network ID cards and has begun piloting in two states. The EU's "European Digital Agenda" released in 2010 also clearly puts forward "enhanced trust, security, and protection of prepaid cardholder data and establish strong authentication". At present, 10 countries in the European Union have started online identity authentication.
It is correct to solve the current problems encountered by the Internet by strengthening the eID management method: when human beings cannot fully manage social networks and manage the Internet, they cannot define the Internet correctly. When they cannot find a matching solution, eID is undoubtedly a kind of The most practical solution. However, I think there is an excellent solution, that is, the "trusted domain" theory.
What is a trusted domain theory?
Before explaining the theory of the trusted domain, we first define the Internet: The Internet is the mapping of human society and even human civilization on the high-speed information platform. Trusted domain theory is derived from this definition. Without this foundation, it cannot breed the theory of trusted domains and the subsequent derivation.
A trusted domain is a collection of trusted identities. The current trusted identities are independently verified and identified by various network service providers. Each Internet customer must log in to the Internet through the service provider portal. It can be said that innumerable entrances have caused a sharp increase in the risk of the Internet. The area in which each service provider on the Internet is responsible is a small trusted domain. These small trusted domains correspond to trusted communities of human society.
The world’s Internet is thus divided into small and credible tribes, which is far behind the real world. Why do you say that? In the real world, I can go to Wangfujing to shop at the same time and I can also freely choose restaurants and theaters to enjoy their services. But on the Internet, can Taobao's customers go to Jingdong to buy a screw? Even if Tencent is willing to open up some of the service providers' log-in portals, it is also a service of the same level, which is difficult to achieve across different levels. For example, QQ customers face obstacles in the level of identity and service synchronization. Some information services only need the user name level identity to obtain, but because QQ opened the login information, may provide the service provider with advanced identities, including payment, QQ customers for their own convenience to hurt their own choice , thus spreading personal privacy.
It may be that readers disapprove of this fragmented service and individual trustworthy tribes, but when credible departments evolved into later stages, the risk emerged. Through smart big data analysis, this customer is fragmented in various service providers, and with the specific information of the Internet IP, I can get a complete information of a customer, including the identity of the real society. What's terrible is that this big data analysis can be used to obtain privacy, such as individual hobby and hobbies that cannot be known even through torture, and even some invisible split personality that one cannot identify.
This is the inevitable result of the current development of the Internet. Customers and service providers are not equivalenced in the security level. The process of service integration has increased the difficulty of protecting the customer's network rights, making the customer's identity information vulnerable to attack. The result is that customers are either The nakedness of the Internet requires that you must have strong professional knowledge and use relatively complicated operations to protect your online rights.
I summed up the defects of the original credible tribe in the original stage as four major blocks: cost (the cost of logging in and registering the security department for repeated construction and customer security protection), security (easily attackable decentralized defense structure), and operations ( Continually complicated technologies have led to a slower promotion of services, a slowdown in the evolution of the Internet, and asymmetry (information, identification, security, means, etc. of customers and service providers).
Advantages and disadvantages of eID management
The government-led eID management in many countries is the crux of the Internet. At the stage where there is no conclusion and corresponding theory in the world, the alternative operation method is first practiced, so the advantages and disadvantages of this solution are obvious.
The biggest advantage of management through eID is that through the authentication and identification technology of the government endorsed, all trusted tribes are opened, and customers can use the unified authentication identity to carry out network life and connect scattered trusted tribes together. This area is a trusted domain, but this is a trusted domain at the same level. In this trusted domain, the service was opened up, which greatly reduced the costs of all parties in the Internet. With the gradual deepening of eID, each new and old service provider shares a customer base, simplifies operations and improves efficiency, and reduces costs while improving the service provider's productivity.
Managing with eID has both advantages and disadvantages. As early as 2011, President Barack Obama put forward a national strategy for online identity cards, also known as the National Cyberspace Trusted Identity Strategy (NSTIC). The most important part of this strategy is the role of the country in the evolutionary process. To effectively protect human rights and sovereignty over the Internet, the government cannot become an authentication and identification agency for this Internet portal, including any major unit or group, and must have a non-profit nature similar to that of the United Nations or notary office. Institutions with the principles of four “public†(open, fair, impartial, and trustworthy) are responsible for this role. This institution generally cannot be set up or designated by the government. The best condition is that the market evolves autonomously to develop such an institution. The state is only responsible for strategic guidance and promotion.
Why can't government departments do authentication and identification of Internet portals? I assume a scenario to deduct. If the entrance authentication and identification institution is a government department, this institution must also have a superior authority, and the practitioners also have a job identity and career path. The human's self-motivation will prompt them to make the option of maximizing their profits. Similarly, those who have the right to manage will have to make full use of these identity data to quickly achieve their goals if they want to deal with competition or crisis during their term of office. Otherwise, they will not be human society. Therefore, even if the transparency is higher in the United States, it also draws a red line, emphasizing the government's role in this area.
Health correctly implements trusted domains
So, how to implement a trusted domain correctly and healthily? The result of my research is that we must first legislate. Without rules, it is impossible to define the bottom line of behavior without legislation. It is difficult to clearly define what is being infringed upon and what should be protected. Only by establishing the basic status of network human rights and sovereignty can the corresponding construction and development paths be developed in turn.
China does not have the right to speak on the root server, but we also need this huge Internet propeller. Then, we must begin to position and price this propeller, and really confirm the development model from any perspective without any selfishness. Both the back door and the speculative mentality will pick up their own feet.
The complete statement of a trusted domain is the identification and authentication system of third-party trusted identities. This system is not to identify who the customer is, just to confirm whether this customer is credible. The trusted domain model is to build a network ecosystem that corresponds to the real society, allowing participants to engage in social activities at a higher speed, rather than controlling participants or controlling participants' behavior. Each participant should have the same free and autonomous rights as in real society. If customers do bad things on the Internet, they will also face the same responsibility as real society. They will not be safer or more dangerous because they are online. This system is to guarantee the equality and synchronization of each client. Its role is to filter anti-rule behavior rather than anti-social behavior.
I emphasize the human rights and sovereignty of the Internet and emphasize the importance of grading identities. This is to better correspond to the actual conditions of the real society. The network society should be more progressive than the actual society, not more backward. This is the principle. A city is a real-world trusted domain. People in the streets are all human. At least they are theoretically trusted. However, they cannot predict the security of their future behavior because their behavior is determined by their own consciousness. In this urban trusted domain, any behavior has the basis for determining their identity. This is also the purpose of the different levels of identification such as student ID, household registration, passport, ID card, and driver's license.
The establishment of a trusted domain will become an upgraded version of the current Internet, just as finding a new continent, the first-mover will certainly have more right to speak, in the premise of improving the level of security to simplify the entry verification process.
At the same time, the truly healthy and sound establishment of the trusted domain model can enable us to guarantee the security evolution of the Internet at a relatively low cost in the current fierce Internet competition, ensure the maximum innovation of the Internet, and deploy more social capital to invest in this field. We can achieve structural transformation from the forefront of the economy, at the same time we can optimize our network security layout, gain the right to speak in the Internet legislation and system construction, gradually change the layout and management structure of the current root server, and achieve a three-dimensional global network structure of the root server matrix. To break all monopoly and demarcation economic activities, so that China's capacity and capacity advantages have been fully played.
SMT Stencils
The sole purpose of an SMT stencil is to transfer solder paste to a bare Circuit Board. A stainless steel foil is laser cut creating an opening for every surface mount device on the board. Once the stencil is properly aligned on top of the board, solder paste is applied over the openings (making a single pass, using a metal squeegee blade). When the stainless steel foil is separated from the board, solder paste will remain, ready for placement of the SMD. This process, as opposed to hand soldering methods, ensures consistency and saves time.
Stainless steel foil thickness and aperture opening size control the volume of paste deposited on the board. Too much solder paste causes solder balling, bridging, and tomb-stoning. A lack of solder paste creates insufficient solder joints. All of which compromise the electrical functionality of the board.
Proper foil thickness is
chosen based on the types of devices being loaded on the board. Component
packages such as 0603 capacitors or 0.020" pitch SOICs, will require a thinner
solder paste stencil than larger packages such as 1206 capacitors or 0.050"
pitch SOICs. Solder paste stencil thickness ranges from 0.001" to 0.030". The
typical foil thickness used on the majority of boards is anywhere from 0.004"
to 0.007".
Now offering nano coating on select stencils and sizes! "Nano
coating" is a two part, wipe on process, made up of hydrophobic elements that
repel flux and solder, resulting in improved paste release for extremely small
components. The coating is applied to the contact side of the stencil prior to
shipment, making the stencil ready to use right out of the box. This coating is
recommended for fine pitch QFN`s, fine pitch IC`s, micro BGA`s, and 0201
component types.
Framed SMT Stencils
Framed Stencils or glue-in stencils are laser cut stencil foils permanently mounted in a stencil frame using a mesh border to tightly stretch the stencil foil taut in the frame. These solder paste stencils are designed for high volume screen printing on printed circuit boards. They are recommended for Printed Circuit Board assembly when doing production runs. Our framed stencils provide optimum solder pastevolume control. Framed stencils have smooth aperture walls and can be used for 16 Mil pitch and below and for Micro BGAs.
Frameless SMT Stencils
Frameless Stencils are laser cut stencilsdesigned to work with stencil tensioning systems also known as Reusable Stencil Frames like the Universal Frame These solder paste stencils do not need to be permanently glued in a frame. Frameless Stencils are significant less expensive than Framed Stencils and reduce storage space requirements.
Frameless Stencils are designed for screen printing on Printed Circuit Boards. They are recommended for prototype printed circuit board assembly or short runs. Our Frameless Stencils provide optimum solder paste volume control. They have smooth aperture walls and can be used for 16 Mil pitch and below and for Micro BGA's.
Prototype SMT Stencils
Prototype Stencils (standard to 10"x12") are laser cut stencils custom-made for your own printed circuit boards using your Gerber Paste file. Comes with a squeegee blade and board holders. These frameless solder paste stencilswere specially designed for manual printing.
Rayming produce Solder Paste Stencils - Laser Cut Stencils,SMT stencils, and offers the largest selection of SMT stencils.
About Us:
BentePCB is a professional PCB manufacturing which is focus on double side, multilayer, HDI PCB , rigid PCB and Flexible PCB mass production. The company was established on 2011.
We have two factories together, The factory in Shenzhen is specialized in small and middle volume orders and the factory in Jiangxi is for big volumn.
Why Us?
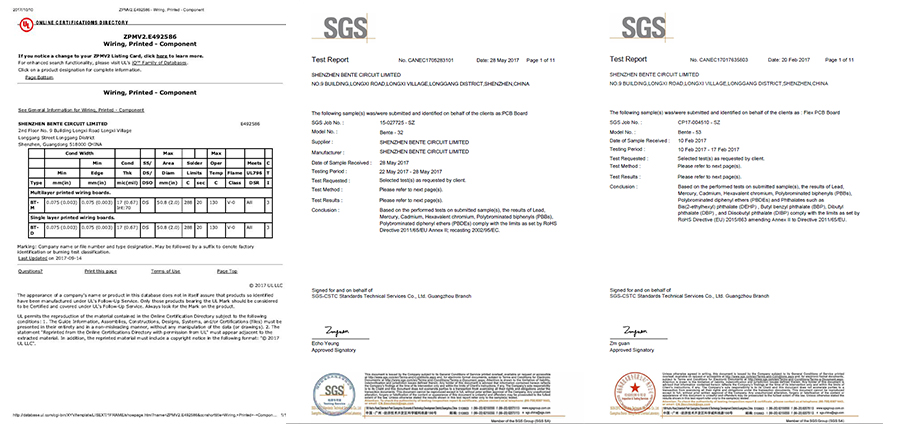
UL (E492586), ISO9001, ISO14001, TS16949, RoHS certified.
Turnover USD 10-50 million per year.
15,000 sqm area, 450 staff .
Mass Production from single to 16 layers.
Special Material:ROGERS, Arlon, Taconic.etc.
Client:Huawei, SAMSUNG, Malata, Midea,Texas Instruments.etc.
Certification(UL:E492586, TS16949, ISO14001, ISO9001,RoHS):

Factory Tour:



Exhibition:
We Took part in the famous exhibitions over the past years,and got highly appreciation from the top experts,as well as cooperated tightly with them.

Delivery:
BentePCB offers flexible shipping methods for our customers, you may choose from one of the methods below.

FAQ:
Q1: What does BentePCB need for a customized PCB order?
A: The customers need to provide Gerber or pcb file.If you do not have the file in the correct format, you can send all the details related to the products.
Q2: What is your quotation policy?
A: For the PCB order in large quantity, BentePCB will send you the quotation based on the MOQ of the products concerned, and the price will be reasonable with good quality.
Q3: How long will you send us quotation ?
A: After all files were sent, 2 to 8 hours as per your file.
Q4:What is your minimum order quantity?
A:Our MOQ is 1 PCS.
Q5: How about the service BentePCB offered to the customers?
A: If you have any questions about our products or company, do not hesitate to send us your inquiry toour customer service representatives, Your satisfaction is our pursuits.

We don`t just sell PCBs .We sell sleep.

SMD Stencil
SMD Stencil, PCB Stencil, SMT Stencil, Stencil Printer
Shenzhen Bente Circuit Limited , http://www.bentegroup.com